DevSecOps professionals always battle against the shifting landscape of cyber threats. One weapon in the arsenal of hackers is the dreaded zero-day exploit. It’s a ticking time bomb that can shatter an organisation’s security posture, especially on the cloud. This blog will narrate all the past incidents, the learnings, and the underlying concepts for you to know more about these Zero Day exploits.
What is a Zero-Day Exploit?
Picture this: a vulnerability in a cloud application, unknown to the world, becomes a hacker’s playground. This is a zero-day exploit—aptly titled because it leaves organizations with ‘zero days’ to react before being exploited. Such attacks are often targeted on cloud-native platforms. They involve pinpointing undiscovered security weak spots. Which are then used as entry points to breach an organisation’s network infrastructure.
The success rate of zero-day attacks is high due to their stealthy nature. Traditional defence mechanisms are often caught off-guard, like sentries facing an invisible assailant, are often caught off-guard. Attackers zero in on vulnerabilities in web browsers and email attachments. These unintentional chinks in the armor are difficult to detect. They allow miscreants to lurk in the shadows for days, months, or even years. Unrestricted, unmonitored, and unfiltered access to all your systems. Or worse, even affecting the users.
In a very fresh Zero Day attack incident, a Salesforce vulnerability was exploited to grab linked user Facebook credentials.
How Do Zero-Day Exploits Work?
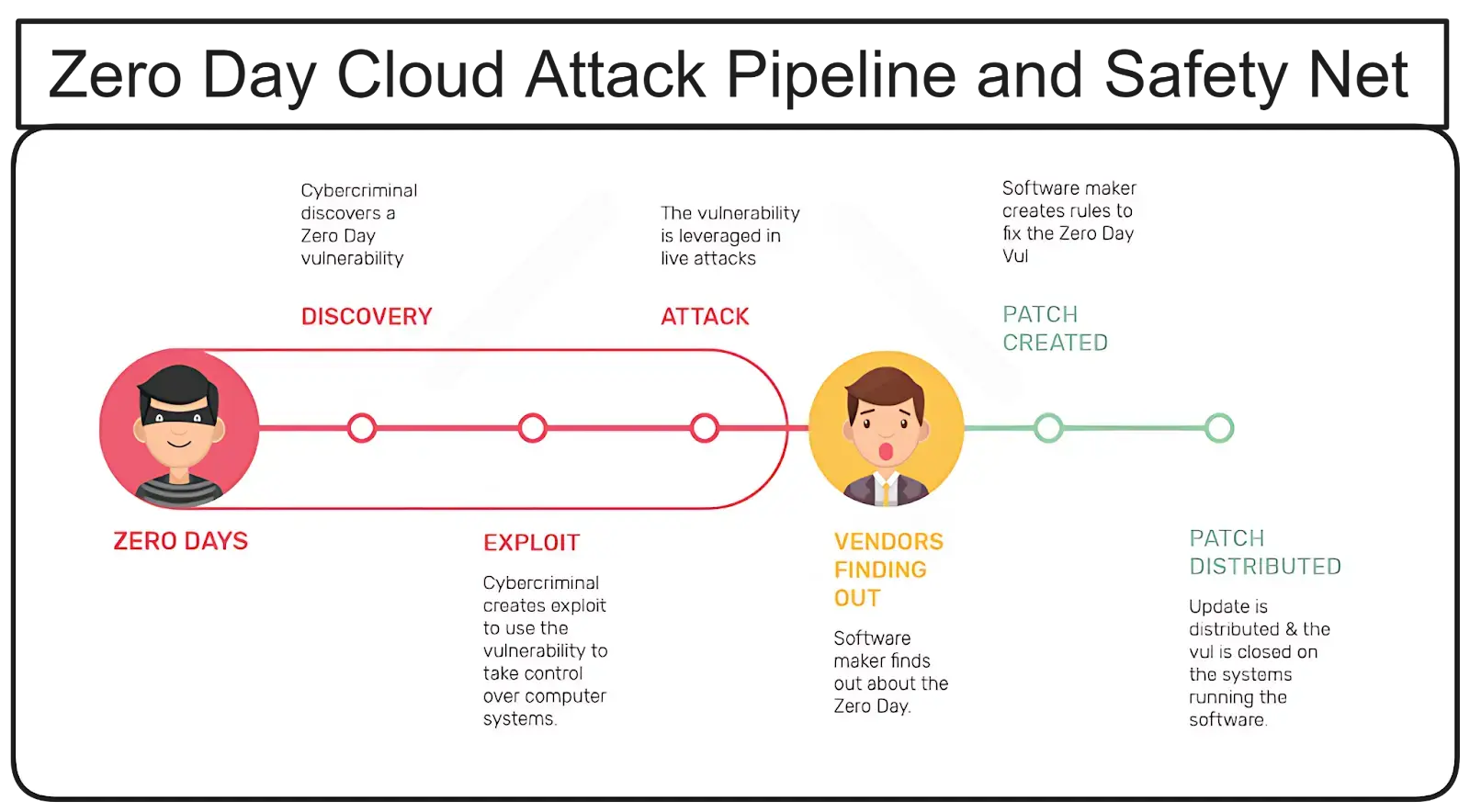
The clock starts ticking the moment a zero-day vulnerability comes to light. It is a race against time. Cybersecurity experts scramble to fortify defences and track potential compromises. Meanwhile, threat actors are already at work. They craft exploits and launch Waves of attacks on unsuspecting targets.
The modus operandi of a zero-day exploit? Identify an uncharted vulnerability and weaponise it. Attackers code malware to exploit specific weaknesses and turn it into a deadly payload. When executed, this malicious code infiltrates a system. This is why you see data breaches, ransomware deployment, or worse.
A usual honeypot is phishing emails with attachments or links that conceal true intentions.
Remember the infamous Sony Pictures Entertainment breach of 2014? A zero-day exploit played a starring role, exposing sensitive data to the public. Unreleased movies, confidential emails, and strategic plans fell into the wrong hands. Even tech giants are not defended against such evolving forms of attacks.
The bad news is that a multiplier is involved for cloud-native apps due to a higher attack surface.
These Zero-Day attacks occur due to weak links in cloud security and failure to prepare damage reports periodically. Here is a handbook of Cloud Security tips for your next internal application review. Consulting this may significantly reduce and weed out such Zero Day vulnerabilities.
Why are Zero-Day Attacks So Devastating?
Zero-day exploits leave a trail of destruction. Notable damage includes:
- Loss of Critical Data. Sensitive information, customer data, and proprietary secrets vanish. Always be backed up.
- Erosion of Trust. Trust takes years to build, yet only moments to shatter. Customers losing faith in an organisation’s security measures can be detrimental.
- Resource Drain. Valuable engineering resources get diverted from innovation to firefighting. Dealing with a zero-day attack isn’t just about plugging the hole.
- API Hacking. They can fool the system by making it believe all systems are healthy and running as expected by overriding API systems or injecting custom code in the rootkit that whitelists a dangerous malware so that it never surfaces. Planning API endpoints with great care needs testing, container security, and healthy deployment of CI/CD pipelines.
For a full narrative, check out the CSO Online article that unveils 55 zero-day exploits and how this has affected security risk management.
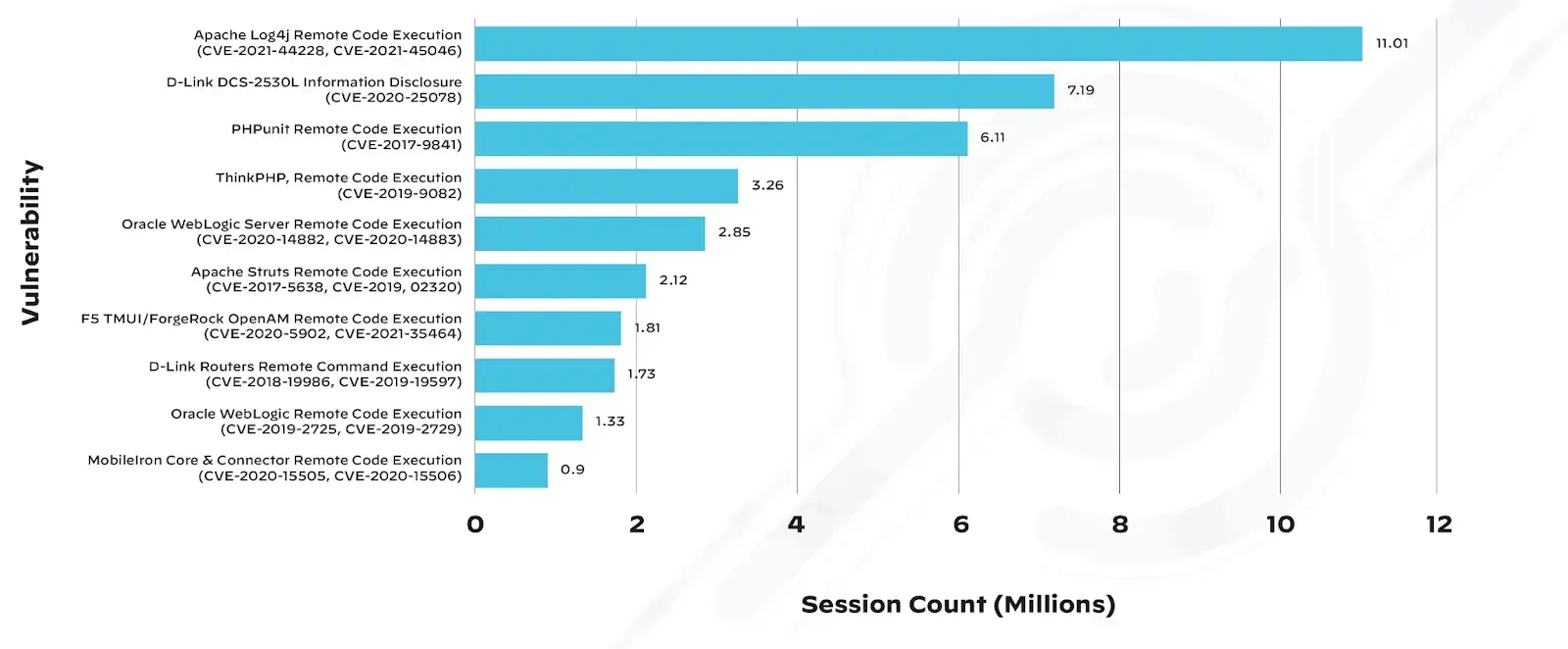
Source: Google Blog
Significance of Zero-Day Exploits in the DevSecOps Landscape
A zero-day exploit is a serious threat in the world of DevSecOps. Before developers can reply, hackers exploit flaws, leaving victims defenseless. The immediate manipulation of vulnerabilities makes zero-day exploits crucial. The development and security teams and have little to no response time. Hackers take advantage of this possibility to migrate laterally within systems. They steal critical information, multiplying the potential harm.
These incidents highlight the seriousness of zero-day exploits. During the 2016 DNC hack, attackers exploited six zero-day vulnerabilities to steal emails from the Democratic National Committee. Researchers predict an increase in zero-day exploits. Projections show development from one vulnerabiexposureek in 2015 to one per day by 2024. Such software vulnerability discoveries drive the development of tendencies. Adobe products had 135 vulnerabilities in 2016. According to the Cybersecurity Ventures 2017 Q1 Report, Microsoft products were featured 76 times. All this can be attributed to the lack of a decent Cloud Native Application Protection Platform (CNAPP) and Zero Trust mismanagement.
The growing reliance on open-source code increases the risk. During a zero-day attack, a weakness in a single block of open-source code deployed across many devices increases the attack surface. In 2019, zero-day attacks accounted for 50% of all malware discovered. 40%+ companies have adopted the Zero Trust security paradigm. They now enable zero-trust network access using remote access VPNs. This highlights the importance of reinventing security paradigms within the DevSecOps ecosystem.
For a full list of exploits to date with a complete breakdown, refer to this exhaustive database by Zero Day Tracking Project
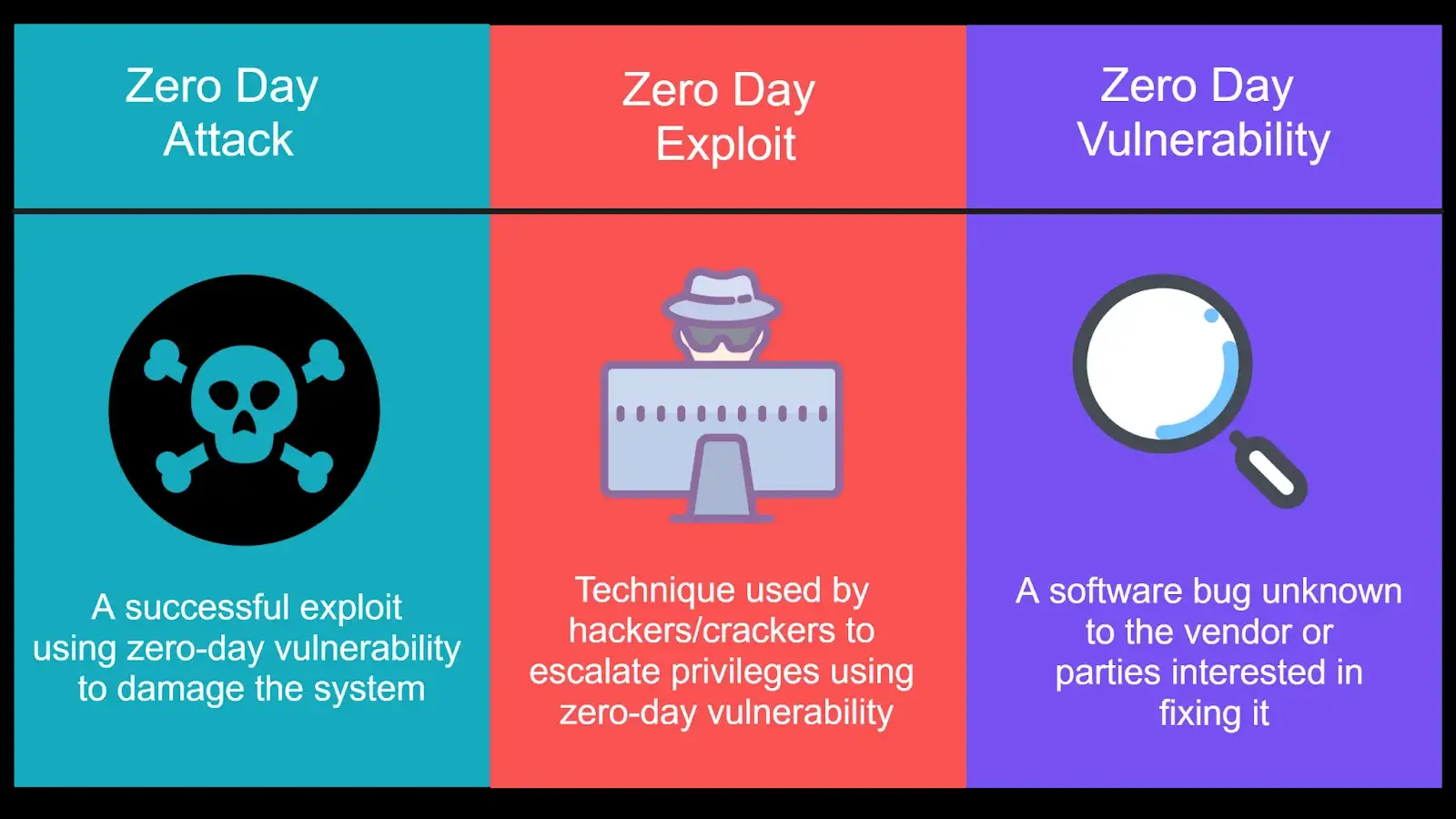
Source: Palo Alto
Techniques for Detection of Zero-Day Threats
Detecting zero-day threats poses a significant challenge due to their elusive nature. Here are key strategies to enhance detection capabilities:
Backed by Statistics
Leveraging machine learning, historical data from past exploits is collected. Real-time monitoring establishes a baseline for safe behaviour. Still, this approach needs to be adaptable to evolving attack patterns. It also requires continuous profile updates.
Based on Behaviour
Analyzing user interactions with software to discern malicious activity. This method predicts network traffic flow by learning expected behavior to block anomalies.
Signature Analysis
A traditional process involves cross-referencing local files and downloads with existing malware signatures. It identifies known threats but needs to improve in detecting novel zero-day threats.
Interested in learning how DevSecOp teams and security engineers strategize and sprint to tackle such exposed threats? Redhat covers this in detail, reviewing the preparation, mitigation, categorization, and rule development. You can take a note from their playbook.
Proactive Zero-Day Attack Prevention
Code vulnerability mitigation needs security from all fronts. A CNAPP that offers CSPM and CWPP with agentless models is a great solution to consider. Important risk-reduction approaches and tools include:
- Browser Isolation : Protects end-user devices and networks from potential risks during surfing by segregating code execution.
- Remote Browser Isolation : Code is loaded and executed on external cloud servers via websites.
- On-premise Browser Isolation : Similar to remote isolation, but performed on servers managed internally.
- Client-side Browser Isolation : Sandboxing ensures the user-device separation of code and content.
- Firewall : An important security system that monitors incoming and outgoing traffic based on predefined policies, protecting trusted networks and data.
Hardware, software, or hybrid firewalls deliver threat prevention by blocking dangerous content and preventing data leakage.
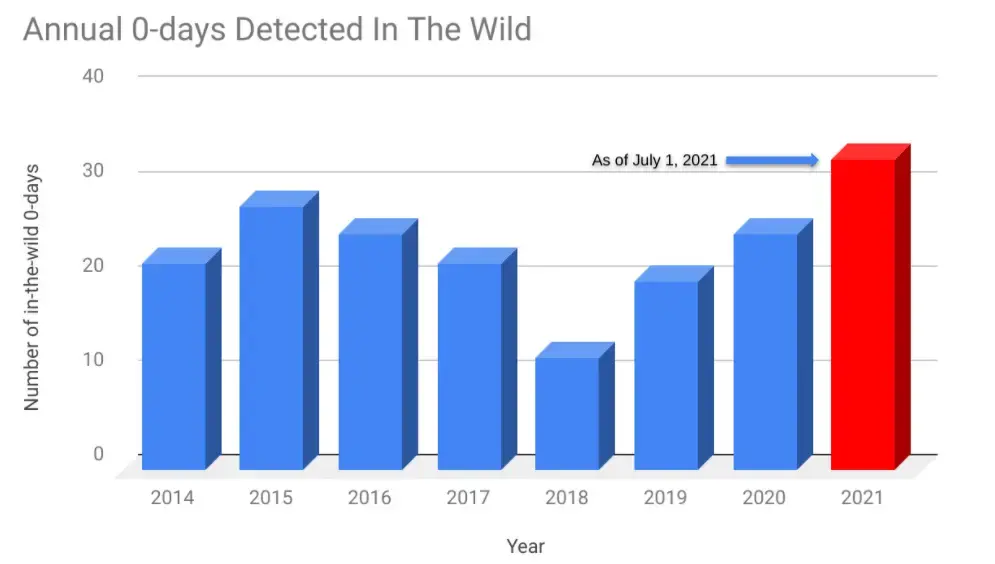
Characteristics of an Optimal Solution
- Do a regulated assessment of existing security architecture to detect potential avenues of entry for cybercriminals. Mandate code reviews to ensure no internal flaws in the system.
- Quick reaction to evolving risks following these techniques input validation. Endpoint security is achieved through code sanitization. Put in place powerful application firewalls.
- Use intelligent behavioural and market analysis to pick cloud security tools.
- Patch Management leads to timely deployment of software fixes. It addresses discovered vulnerabilities.
- Secure connections for microservices, containers, and APIs across several cloud platforms. For real-time threat detection, use threat intelligence powered by AI.
- Defend against spam and malware with email monitoring, 24x7 threat analysis, IP reputation filtering, and antivirus engines.
The best cloud security tool selection is a strategic choice that requires serious thought. Making educated selections is made easier by using behavioural and market analysis. Find a balanced solution that meets your infrastructure’s needs while also being in line with security goals by consulting a CNAPP Buyer’s Guide.
Conclusion
Detecting and avoiding zero-day threats in DevSecOps requires a mix of modern tools and behavior analysis. Robust protection involves using methods like statistics-based, signature-based, and behavior-based detection. Browser isolation and firewalls also help. As discussed, the ideal system includes vulnerability detection, input validation, security planning, patch management, business infrastructure security, and spam/malware protection. DevSecOps teams may significantly reduce monetary losses and customer paranoia following these techniques.
