Understanding Microservice Architecture
Grouped services are used to implement an application in a microservice architecture. Development teams these days favour microservices. This is because large apps get delivered continuously without interruption. Since it is a cloud-based approach, the tech stack scales up based on demand. Single-tier monolithic systems are simpler to set up fast. They interface with popular frameworks, tools, and IDEs. However, monolithic apps’ flaws start to become clear as they age.
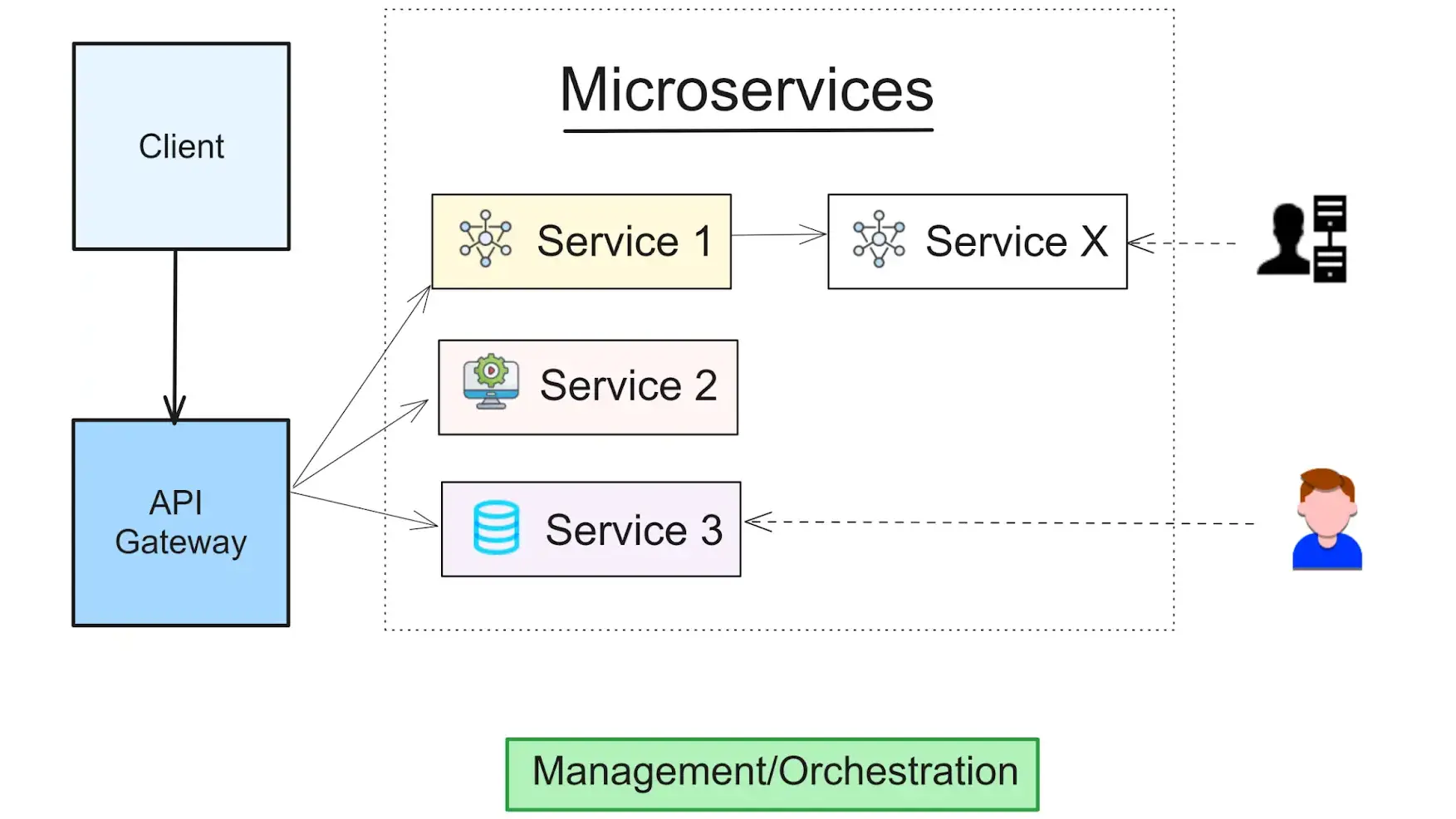
Microservices are independent programs grouped to form the user-facing functionality. Systems are built as a single monolithic component. It takes care of all the features of microservices are not. But, with a microservices design, members are deployed individually. They are responsible for certain subsystems, and interfaced networking is added for better communication. The app calls the authentication service, payments platform, and other components. It’s done by using the backend APIs.
The microservices paradigm presents potential ports of entry for vulnerabilities in your system. A broader attack surface means better chances for attackers. A Cloud-Native Application Protection Platform (CNAPP) solution that offers protection for each microservice and the links between them is well-suited for workload protection and hardening. Missing this allows lateral movement to services in the event of an attack against one route. E.g. web API or authentication service.
The size distributed systems can reach poses another cloud security concern for microservices. In practice, most systems offer more than just the web API, authentication service, and payment platform. Introduce as many service splits as possible to profit from a microservices design. Systems these days consist of hundreds of distinct parts. Each of these is deployed as a separate microservice. There is more potential for error when there are so many moving pieces. Because of this, focus on securing every service fully.
Security Drawbacks of Microservices in the Cloud
A microservices design is usually more secure than a monolithic application. Due to its decoupled nature, vulnerabilities only affect a single component instead of the entire application. Microservices may pose extra cloud security risks due to their complexity. Every standalone module needs to have inter-service communication. This demands thorough testing and monitoring. Let us understand the security issues raised by the deployment of microservice architecture. Here are the ones you should be concerned about DevSecOps The development and operations teams work together to execute a successful microservice architecture. They must be knowledgeable about the protocols and any security risks. Designing, coding, distributing, and maintaining are separate stages of application development. Still, the apps are released without thorough testing, and security issues appear. Microservice-driven cloud computing workload is more agile and secure. Apps may not have undergone adequate testing due to frequent development iterations.
Need for Better Logging
The ecosystem of DevOps microservices is quite dispersed. Distributed and stateless microservices generate more logs as a result of their independence. Finding new issues can be challenging if there are many logs. Centralized logs should be sent to a single external destination for effective logging and coordinating user log events across platforms. This calls for a more elevated perspective that does not rely on any particular API or service.
Isolation with Segmentation
This is a key rule for a program built on the microservices architecture. A microservices-based application should be developed, tested, extended, deployed, and maintained separately from one another. They cannot interfere with the operation of any other parts. This will make the core philosophy void. Additionally, database-level isolation is advised. To prevent one service from knowing how another uses its data, it is necessary to separate the data for each microservice. You can increase the security of your microservices-based program by requiring layer-by-layer isolation.
Higher Surface of Attack Vectors
Due to many open ports and exposed APIs, the attack surface expands sharply. These APIs are more vulnerable to attacks since each microservice interacts with one another. All microservices must be hardened to counter this security issue.
Fault Tolerance
Installing fault tolerance in microservices-based applications is far more complex than monolithic programs. Services must be resilient to timeouts and disruptions. Other services may experience aggregated failures if this form of service failure persists. Thus, fault tolerance is crucial to be able to recover from interruptions. If not, it can make your entire application unstable.
Strategies to Secure Microservices in Multi-Cloud Platforms
Adopting security measures is the only tactical action. It improves the application’s agility, scalability, and resilience. Security is enhanced without jeopardizing communication across individual Microservices. This is because each microservice has its endpoints. For a secure microservices ecosystem, use these 7 strategies.
Design with Security in Mind
Most application architectures depend on microservices when replacing large-scale, legacy systems. This offers an ideal opportunity to improve the security of current systems. To understand security procedures and how to address any security issues early on, the focus should be on building relationships with all the stakeholders and security groups. This is in contrast to putting security into place once the software is almost finished. It is easier, more effective, and less expensive.
Use API Gateway
Only clear and safe APIs should be used for communication between microservices. API gateways serve as a single data entry point and direct it to the proper microservices. The API gateway frequently uses token-based authentication to limit services’ access to and usage of data. Putting the API gateway behind a firewall is advised to increase security. Adding this will add an extra layer of protection. It also ensures that every microservice used in a particular application is secure.
Deep Defense Practice
To ensure their security is impenetrable, go with a defence-in-depth approach. Numerous layers of security controls and the “defence in depth” strategy increase the security of its software. Add technical controls; these can be:
- Firewalls
- Intrusion detection schemas
- Anti-virus
- Multi-wall access restrictions
Tighten them with non-technical approaches like rules, compliance, and team upskilling. Microservices design requires multiple layers of cloud-native application protection platform (CNAPP) to defend vulnerable areas. This multi-layered strategy means a greater assurance without unnecessary complexity.
Security for Containers
Containers have emerged as a preferred option for teams struggling with the complexity of microservice-based apps. Streamline deployments and improve overall efficiency with containers. Microservice security is backed only by container security. It eases the application of cloud-native security solutions. Containers’ security goes well beyond the images upon which they are based. The platform comprises the orchestration tools and the container registry, which houses pictures. Monitoring the container registry for weak images is essential to reducing the possibility of many microservices using the same base image. Eliminate misconfigurations and other potential dangers for a more secure microservice deployment.
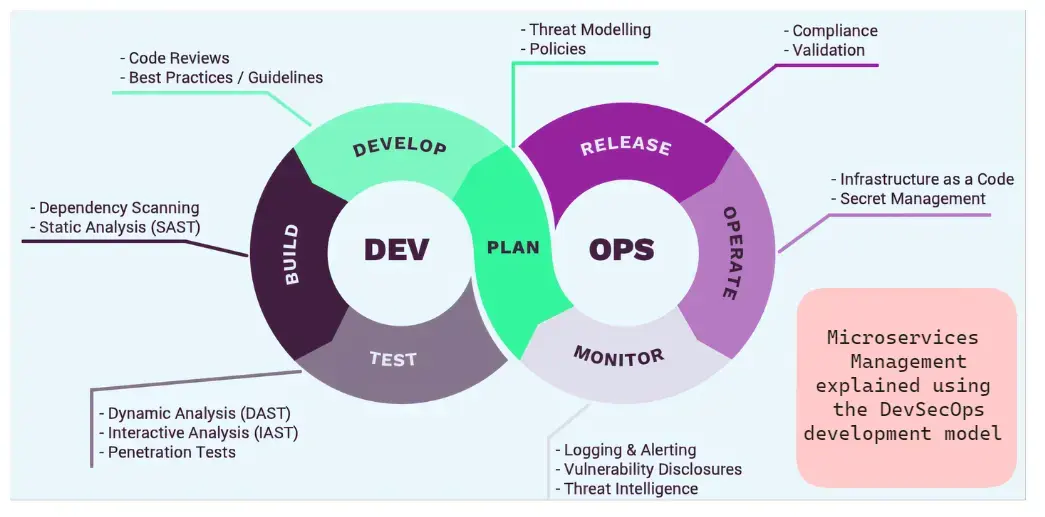
Adopt a DevSecOps approach
Microservices allow for quicker software releases, expediting application creation for DevOps teams. But this raises security concerns. A DevSecOps approach that integrates security controls into the development process and builds environments should be adopted. It will ensure software security without delaying the process. This way, the focus will be on software reliability and security. The development process will be timely.
Investigate dependencies
A microservice architecture uses open-source components. These outperform the development team’s original code. There is an increasing reliance on third-party dependencies. This introduces vulnerabilities that impact the app’s risk profile. If these packages are not tracked properly, a vulnerability in one can be exploited. Using an open-source security management tool can help identify and fix security issues in software.
Multi-factor authentication keeps you safe
Microservices security protects endpoints and frontend applications. User authentication and access control are the most critical parts. Multi-factor authentication (MFA) is a successful tactic for blocking fraudulent behaviour. Users must complete a two-step authentication process to access accounts using OAuth2 or JSON Web Tokens. An effective MFA process can raise a red flag for questionable activity.
When To Avoid Cloud Microservice Architecture?
First, assess the application’s requirements and the team’s capabilities. Microservices are generally advantageous for distributed and complex apps. However, they are only sometimes universally applicable solutions. Following are some circumstances in which microservices should be avoided:
- For basic applications that don’t need high scalability or modularity.
- Suppose an application’s components are interdependent and tightly tied. It is easier to divide them by altering the application’s design.
- Adopting too much traffic calls for more infrastructure, development, and operational resources. All these are in short supply in rapid prototyping. With sufficient resources, managing and tool microservices might be possible.
- An application must receive a high traffic volume to ensure the benefits of microservices, such as scalability and fault tolerance, are unnecessary. When a business is unprepared to undertake serious DevOps work, it will not be a good fit.
